As a result of that, I'm looking forward to sharing these thoughts somewhere else. It might be pretty soon. Not that LJ hasn't been great - but there are obvious reasons to move on.
As long as I'm dropping oblique hints, I was talking to
Read that document. It's a good one.
For context, though, look specifically at this diagram:
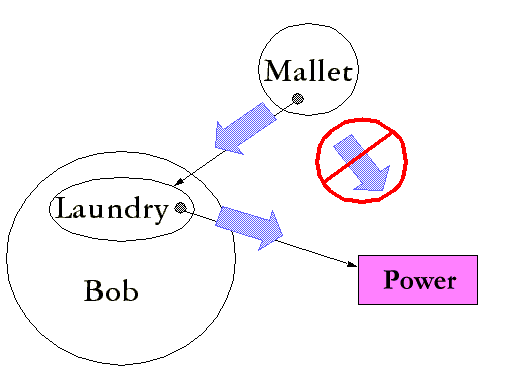
While from a security perspective, the author is technically correct, from a user interface perspective, he's got the issue backwards. The author of this diagram seems to be implying that each of the arrows has equivalent cost. In fact, they do not. If the system openly exposes the ability for bob to grant the power directly to mallet, then the mallet -> power path is effectively of zero cost to bob. However, if it does not, bob has 3 choices to create his message laundry:
- Trust Mallet implicitly, giving him Bob's authentication credentials.
Cost: Bob is now completely at Mallet's mercy, as far as the system is concerned; he has all of Bob's power now. This is probably a situation that Bob wishes to avoid. - Manually launder all messages, using copy/paste or written instructions from mallet.
Cost: Bob has to effectively be Mallet's slave, as far as the system is concerned. This will probably annoy Bob pretty quickly. - Write a message proxy which runs on Bob's computer and that Mallet can connect to.
Cost: Bob has to start a software company and produce a piece of software. This is more expensive than most people imagine. Even if you assume the software already exists, Bob still has to pay for bandwidth for all of Mallet's messages.
I believe cryptographic math may have lead programmers' thinking about security astray. Security is not a hard mathematical problem, as crypto implies: it is simple arithmetic. Security is not about making cipher-breaking completely impossible: people make cipher-breaking impossible because that is a relatively easy way to increase certain kinds of security. Security as a whole, though, is an economic problem. It's about making the cost of an attack exceed the benefits from a successful one. If you can trend the cost/benefit ratio towards infinite cost and zero benefit, then you are successfully making the system more secure. After all, physical security is impossible to achieve with the same perfect mathematical certainty that cipher security is - not even close - yet, people still put locks on their doors.
In the case of a chat application, it is a potentially annoying feature to allow users to delegate their interpersonal authority. In the rather long (in internet terms) life of AOL's instant messenger service, no-one (to my knowledge) has bothered to write a chat-proxy bot that would allow the sort of message laundry described above.
I'm curious what other capability thinkers have to say about this, though.
I hope to have some more time to think out loud about this, especially about the implications of cost as measured in spent attention. The internet era is creating a new commodity: attention. There are very few tools for managing and trading it. Right now, attention is measured in "eyeballs", as advertisers say, but that will change, as the personal and professional consequences of spending too much attention in the wrong place become socially apparent. Will you be more reluctant to pay attention if you can measure that attention in dollars first?
That's it for now, though.




